In today’s interconnected digital landscape, distributed ecosystems play a pivotal role in enabling seamless collaboration and resource sharing across geographically dispersed systems. These ecosystems rely heavily on clusters, which serve as the backbone of distributed environments by clustering multiple nodes to work together as a single system.
However, with this increased connectivity comes a heightened risk of security threats and vulnerabilities. In this article, we delve into the imperative of robust cluster security within distributed ecosystems, exploring the challenges, strategies, best practices, and monitoring techniques essential to fortifying the security posture of these dynamic environments.
Introduction to Distributed Ecosystems:
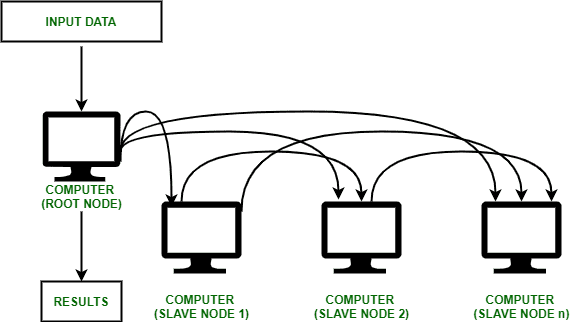
Defining Distributed Ecosystems
In the digital realm, distributed ecosystems refer to interconnected networks of multiple nodes or systems that work together to achieve a common goal. These decentralized structures enable efficient data processing and resource sharing across various locations. When it comes to securing distributed ecosystems, the focus on cluster security becomes paramount.
Without robust security measures in place, the interconnected nodes and systems within these ecosystems are vulnerable to various cyber threats. By ensuring the security of clusters, organizations can mitigate risks and safeguard their data, applications, and overall system integrity.
Role of Clusters in Distributed Environments
Clusters play a pivotal role in distributed environments by grouping together individual nodes into cohesive units. These clusters facilitate streamlined communication, parallel processing, and fault tolerance, making them essential components of robust distributed systems. Clusters serve as the backbone of distributed environments, providing the foundation for efficient data processing and resource management.
By ensuring the security of clusters, organizations can maintain the stability and reliability of their distributed systems, ultimately enhancing the overall performance and resilience of their operations.
Importance of Cluster Security in Distributed Environments
Risks of Inadequate Cluster Security
Insufficient cluster security exposes distributed ecosystems to a myriad of threats, including unauthorized access, data breaches, and potential system malfunctions. Neglecting security measures can result in dire consequences for the overall integrity and functionality of the system. Effective cluster security not only protects against external threats but also safeguards against internal vulnerabilities that may arise within the system.
By implementing robust security protocols, organizations can proactively mitigate risks and prevent potential security breaches. This proactive approach not only enhances the overall security posture of the distributed environment but also instills confidence in stakeholders regarding the reliability and integrity of the system.
Impact of Security Breaches on Distributed Systems
Security breaches in distributed systems can have far-reaching effects, leading to data loss, operational disruptions, reputational damage, and financial losses. Safeguarding clusters against potential breaches is crucial to maintain the reliability and confidentiality of the entire ecosystem. Implementing proactive security measures not only helps prevent security breaches in distributed systems but also minimizes the potential impact of any breaches that do occur.
By continuously monitoring and updating security protocols, organizations can stay ahead of evolving threats and mitigate risks before they escalate. This proactive approach not only enhances the overall security posture of the distributed environment but also instills confidence in stakeholders regarding the reliability and integrity of the system.
Common Security Challenges in Distributed Clusters

Scalability Issues in Security Measures
One of the primary challenges in securing distributed clusters is ensuring that security measures can scale effectively as the system grows. Balancing security protocols with system performance and resource constraints poses a significant challenge for maintaining robust protection across expanding distributed environments.
Addressing scalability issues in security measures is crucial for maintaining the overall security posture of distributed clusters. As the system expands, it becomes increasingly challenging to ensure that security protocols can effectively protect against potential threats. Finding a balance between security and performance is key to mitigating risks and safeguarding the integrity of the system.
Communication and Coordination Challenges
Securing communication channels and ensuring seamless coordination among distributed clusters can be complex. Maintaining data integrity, confidentiality, and authentication in a decentralized environment requires strategic planning and robust protocols to mitigate potential vulnerabilities. Effective communication and coordination are essential components in ensuring the overall security of distributed clusters.
By establishing clear communication channels and implementing efficient coordination strategies, organizations can enhance their ability to detect and respond to potential security threats in a timely manner. Additionally, fostering a culture of collaboration and information sharing among team members can further strengthen the security posture of the system.
Strategies for Fortifying Cluster Security
Encryption and Data Protection Techniques
Implementing robust encryption protocols and data protection mechanisms is essential for safeguarding sensitive information within distributed clusters. Secure transmission and storage of data through encryption technologies help prevent unauthorized access and mitigate the risk of data breaches. Furthermore, regular security training and awareness programs for team members can help reinforce the importance of security practices and protocols within the cluster environment.
By educating employees on potential security threats and best practices for mitigating risks, organizations can create a more vigilant and proactive security culture. This, in turn, can significantly reduce the likelihood of security incidents and breaches within the distributed ecosystem.
Access Control and Authentication Methods
Deploying stringent access control measures and authentication methods strengthens cluster security by regulating user permissions and verifying user identities. Implementing multi-factor authentication, role-based access controls, and regular security audits enhance the overall protection of distributed ecosystems against unauthorized access attempts.
Furthermore, by implementing encryption protocols and secure communication channels, organizations can ensure that data transmission within the distributed ecosystem is protected from interception and tampering. Additionally, regular security updates and patches should be applied to all systems and software components to address any potential vulnerabilities and mitigate the risk of exploitation by malicious actors.
Implementing Robust Security Measures in Distributed Ecosystems
Security Architecture Design for Distributed Clusters
When it comes to fortifying distributed ecosystems, a robust security architecture is the cornerstone of defense. When it comes to fortifying distributed ecosystems, a robust security architecture is the cornerstone of defense. Designing a security architecture tailored to distributed clusters involves understanding the unique challenges and vulnerabilities of such environments. By implementing measures such as network segmentation, encryption protocols, and access controls, organizations can create a resilient security framework that mitigates risks effectively.
Furthermore, staying ahead of cyber threats requires constant vigilance and adaptation. Organizations must continuously assess their security posture and update their defenses to address emerging risks. This proactive approach, combined with ongoing training and awareness programs for employees, can help bolster the overall security posture of distributed ecosystems.
Designing a security architecture tailored to distributed clusters involves understanding the unique challenges and vulnerabilities of such environments. By implementing measures such as network segmentation, encryption protocols, and access controls, organizations can create a resilient security framework that mitigates risks effectively.
Integration of Security Tools and Technologies
In the ever-evolving landscape of cybersecurity threats, the integration of cutting-edge security tools and technologies is non-negotiable. From intrusion detection systems to endpoint protection solutions, leveraging a comprehensive suite of security tools can enhance the defense mechanisms of distributed clusters. By adopting a layered approach to security, organizations can strengthen their resilience against cyber threats.
In order to effectively integrate security tools and technologies, organizations must prioritize ongoing training and education for their IT teams. Keeping abreast of the latest trends and developments in cybersecurity is essential for implementing best practices and staying ahead of emerging threats. By investing in continuous learning and skill development, organizations can ensure that their security measures remain robust and effective in the face of evolving cyber risks.
Best Practices for Securing Distributed Clusters
Regular Security Audits and Vulnerability Assessments
The adage “prevention is better than cure” holds true in the realm of cybersecurity. Conducting regular security audits and vulnerability assessments is imperative for identifying weak points in distributed clusters. By proactively addressing vulnerabilities and implementing patches, organizations can bolster their security posture and stay one step ahead of potential threats.
Implementing robust security measures such as encryption, access controls, and multi-factor authentication is also essential for safeguarding distributed clusters. These measures can help prevent unauthorized access and data breaches, ensuring the confidentiality and integrity of sensitive information. Additionally, regularly updating security policies and procedures to align with evolving threats and industry best practices is key to maintaining a strong defense against cyber attacks.
Training and Awareness Programs for Cluster Users
In the fight against cyber threats, human error remains a significant challenge. Empowering cluster users with training and awareness programs on cybersecurity best practices is crucial for promoting a culture of security within organizations. By fostering a security-conscious mindset among users, organizations can reduce the likelihood of security breaches stemming from inadvertent actions.
Implementing regular security audits and assessments is another crucial aspect of maintaining a secure cluster environment. By conducting periodic evaluations of security controls, organizations can identify vulnerabilities and gaps in their defenses, allowing them to take corrective actions promptly. These assessments also help in ensuring compliance with industry regulations and standards, further enhancing the overall security posture of the cluster.
Monitoring and Maintaining Security in Distributed Environments

No security strategy is complete without a robust incident response and recovery plan. In the event of a security breach or cyber attack, having predefined processes and protocols in place is essential for containing the incident and minimizing its impact. By conducting regular drills and simulations, organizations can refine their response capabilities and ensure swift recovery in the face of adversity. When it comes to incident response and recovery planning, proactive measures are key.
This includes not only having a plan in place, but also regularly testing and updating it to ensure its effectiveness. By staying ahead of potential threats and constantly improving response capabilities, organizations can better protect themselves against cyber attacks and security breaches. Additionally, collaboration and communication among all stakeholders is crucial in executing a successful incident response and recovery strategy.
Conclusion
In conclusion, fortifying distributed ecosystems requires a multi-faceted approach that encompasses robust security measures, best practices, and vigilant monitoring. By prioritizing security at every level of the distributed infrastructure, organizations can safeguard their data, systems, and reputation in an increasingly hostile digital landscape.In conclusion, ensuring the security of distributed clusters is not just a best practice but a necessity in today’s digital landscape.
By implementing robust security measures, staying vigilant with monitoring, and adhering to best practices, organizations can fortify their distributed ecosystems against potential threats and vulnerabilities. With a proactive approach to cluster security, businesses can safeguard their data, maintain operational continuity, and uphold the integrity of their distributed systems in the face of evolving cyber risks.
Also read our blog on The Future of Biometric Security in Cybersecurity

